How you can reverse engineer .NET application
You will learn what is reverse engineering, how .net source compiled into an application and how to reverse engineer it.
What is reverse engineering?
Before we discuss reverse engineering, let’s first define engineering. Engineering is the process of building a solution. Now, what is reverse engineering? It is the process of analyzing and understanding the methods and techniques used to build a solution.
This concept is widely applied in various fields. For example, it can be used to study and understand how nature works. At the same time, hackers often use this method to exploit vulnerabilities in applications.
What is Compilation?
In the software world, your computer does not understand human languages. Computers only understand 1s and 0s because they are electronic devices that use electric current to communicate. With the help of tiny transistors, computers process instructions in binary (1s and 0s) and produce results as another set of 1s and 0s. However, humans cannot easily understand this binary language.
To bridge this gap, humans write code using programming languages that are closer to natural language. These programming languages are then converted into machine code (binary) that computers can execute.
Compilation is the process of translating an entire program into machine code at once. This machine code can then be executed directly by the computer. In contrast,
interpretation is another method of translation where the program is converted into machine language line by line as it runs.
How .NET Applications are compiled ?
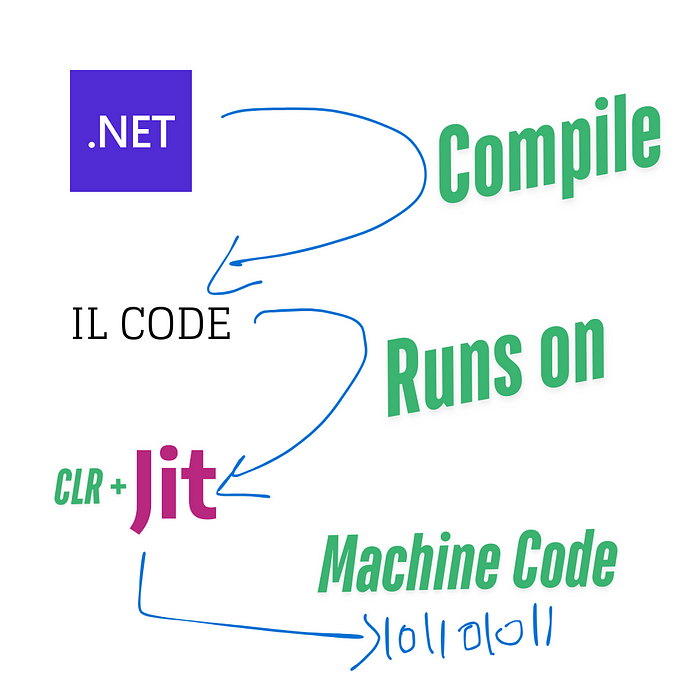
.NET applications are compiled through a multi-step process that transforms high-level source code into machine-readable instructions.
- Developers write applications in high-level languages like C#, VB.NET, or F#, which are human-readable and use the .NET Framework or .NET Core libraries.
- The .NET compiler (e.g, cse.exe for C#) compiles this code into Intermediate Language (IL), a CPU-independent, low-level language that abstracts assembly language. IL enables cross-platform compatibility by allowing the same code to run on different architectures with the help of the runtime.
- The output of this step is an assembly, typically in the form of an EXE for executable applications or a DLL for libraries. The IL, the .NET compiler generates metadata that includes information about types, method signatures, and references to other assemblies.
- When the application is executed, the Common Language Runtime (CLR) compiles the IL into native machine code specific to the operating system and CPU architecture through Just-In-Time (JIT) compilation, optimizing performance by compiling only the parts of the application being executed. In some cases, Ahead-of-Time (AOT) compilation can be used to precompile IL into native code before execution, improving startup performance with tools like ReadyToRun (R2R) or producing standalone executables using Native AOT (introduced in .NET 7).
Once compiled to native code, the application runs on the host system, with the CLR managing memory allocation, garbage collection, exception handling, security, and type safety.
How to reverse engineer .NET Applicatin ?
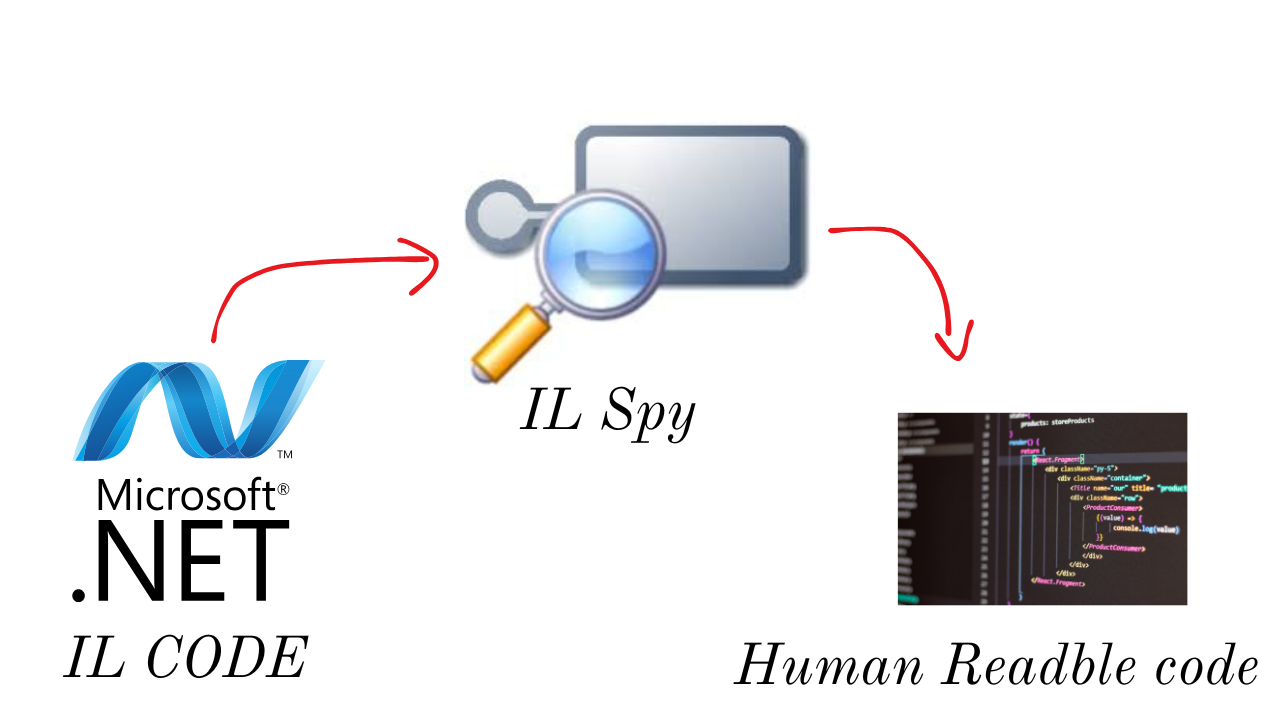
Since .NET application is compiled into IL code and it stored in assemblies with metadata. reverse engineering process make easy.
You can use several decompiling tools, but I’m using ILSpy for this blog.
- Download and install the official tool using below link,
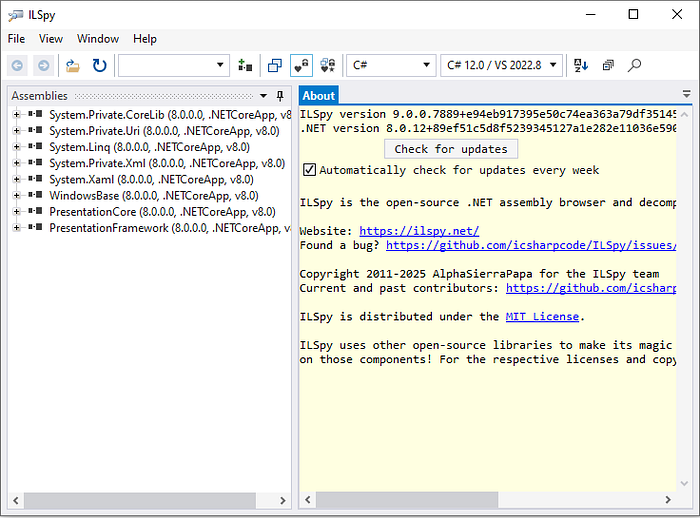
- Open ILSpy You will see something similar to below image
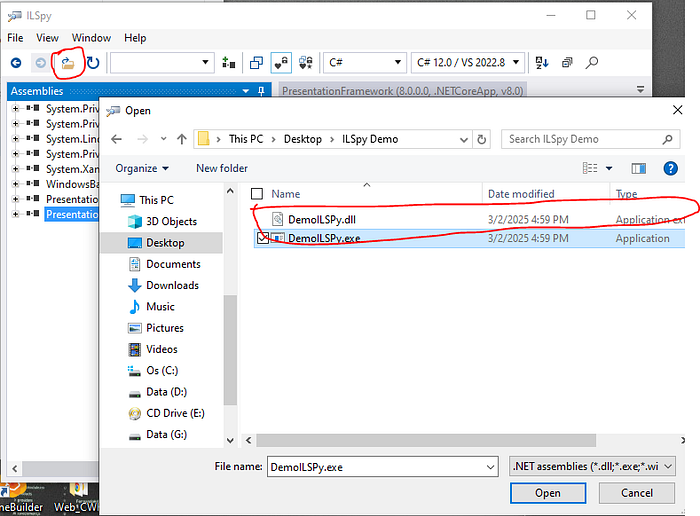
- Using Folder Icon open you exe file written on .net or dll file,
- When you open you will see your source code

- Let me go for a specfic method I have written
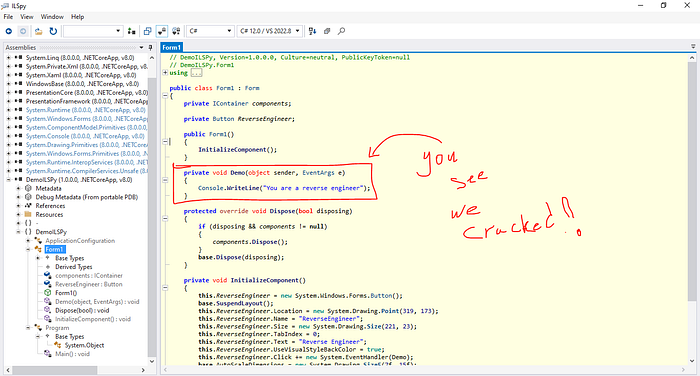
In this way that you have seen we can see everything which programmer is written.
Conclusion
Reverse engineering .NET applications is a process that allows you to analyze and understand how an application was built by decompiling its Intermediate Language (IL) code. With tools like ILSpy, you can easily inspect the source code, understand the logic, and learn about the structure of the application. While reverse engineering is a powerful technique for learning and debugging, it should always be done responsibly and within the boundaries of the law.
